Blobrunner - Apace Debug Shellcode Extracted During Malware Analysis
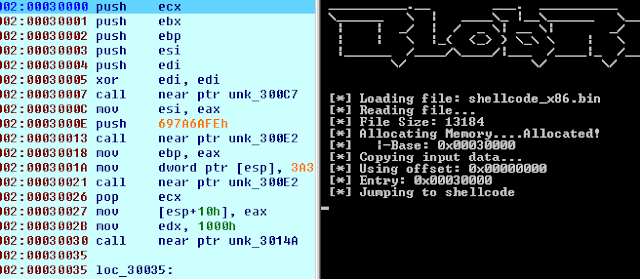
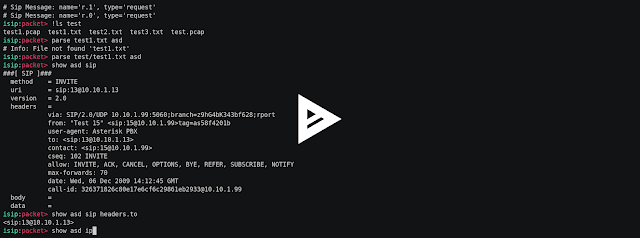
BlobRunner is a uncomplicated tool to speedily debug shellcode extracted during malware analysis. BlobRunner allocates retentivity for the target file in addition to jumps to the base of operations (or offset) of the allocated memory. This allows an analyst to speedily debug into extracted artifacts amongst minimal overhead in addition to effort. To role BlobRunner, you lot tin download the compiled executable from the releases page or fix your ain using the steps below. Building Building the executable is conduct forrad in addition to relatively painless. Requirements Download in addition to install Microsoft Visual C++ Build Tools or Visual Studio Build Steps Open Visual Studio Command Prompt Navigate to the directory where BlobRunner is checked out Build the executable past times running: cl blobrunner.c Building BlobRunner x64 Building the x64 version is most the same equally above, but only uses the x64 tooling. Open x64 Visual Studio Command Prompt