Aes-Killer V3.0 - Burp Plugin To Decrypt Aes Encrypted Traffic Of Mobile Apps On The Fly
Burpsuite Plugin to decrypt AES Encrypted traffic on the fly.
Requirements
- Burpsuite
- Java
Tested on
- Burpsuite 1.7.36
- Windows 10
- xubuntu 18.04
- Kali Linux 2018
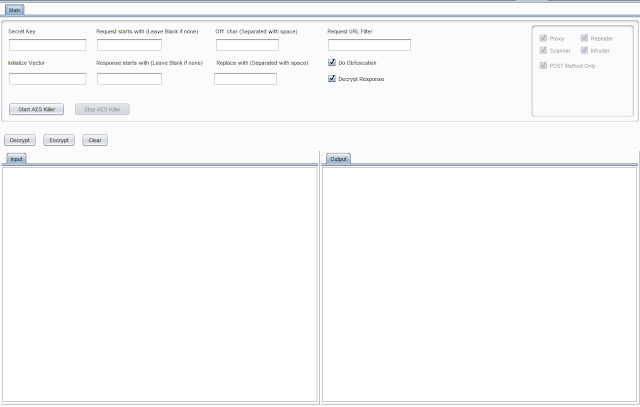
What it does
- The IProxyListener decrypt requests too encrypt responses, too an IHttpListener than encrypt requests too decrypt responses.
- Burp sees the decrypted traffic, including Repeater, Intruder too Scanner, simply the client/mobile app too server come across the encrypted version.
AES/CBC/PKCS5Padding encryption/decryption.How it works
- Require AES Encryption Key (Can move obtained yesteryear using frida script or reversing mobile app)
- Require AES Encryption Initialize Vector (Can move obtained yesteryear using frida script or reversing mobile app)
- Request Parameter (Leave blank inward illustration of whole asking body)
- Response Parameter (Leave blank inward illustration of whole reply body)
- Character Separated amongst infinite for obfuscation on request/response (In illustration of Offuscation)
- URL/Host of target to decrypt/encrypt asking too response
How to Install
Download jolt file from Release too add together inward burpsuiteOriginal Request/Response
Getting AES Encryption Key too IV
- First setup frida server on IOS too Android device.
- Launch Application on mobile device.
- Run this frida script on your host car to popular off AES Encryption Key too IV.
Decrypt Request/Response
- Provide SecretSpecKey nether
Secret Keyfield - Procide IV nether
Initialize Vectorfield - Provide Host/URL to filter asking too reply for encryption too decryption
- Press
Start AES Killer