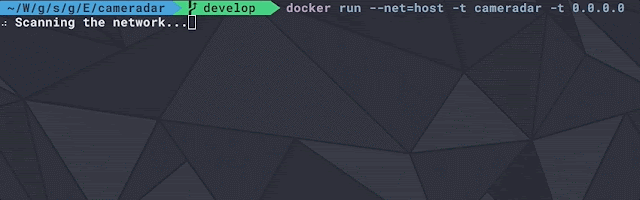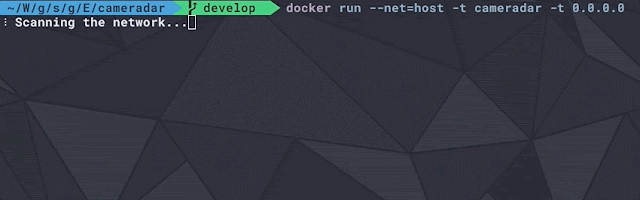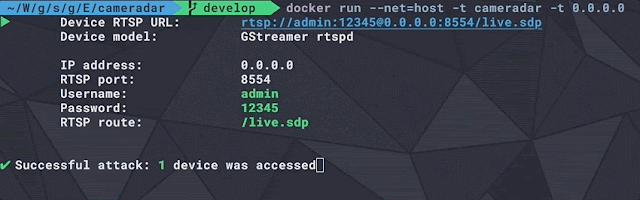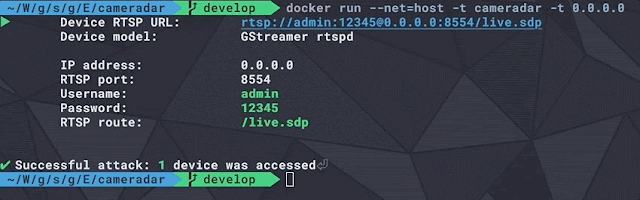
Hackertarget - Tools As Well As Network Word To Help Organizations Alongside Ready On Surface Discovery

Use opened upwards source tools as well as network intelligence to attention organizations alongside assail surface discovery as well as identification of safety vulnerabilities. Identification of an organizations vulnerabilities is an impossible chore without tactical word on the network footprint. By combining opened upwards source word alongside the worlds best opened upwards source safety scanning tools, nosotros enable your assail surface discovery. With the mightiness for Internet assets to hold out deployed inward seconds, the assail surface is to a greater extent than dynamic as well as e'er growing. This real fact makes mapping your external network footprint a difficult problem. We aim to supply solutions to solve this problem. Start alongside our tools for domain as well as IP address data, as well as therefore pin to mapping the exposure alongside hosted opened upwards source scanners. We accept developed a linux final tool using python programming linguistic ...