Blobrunner - Apace Debug Shellcode Extracted During Malware Analysis
BlobRunner is a uncomplicated tool to speedily debug shellcode extracted during malware analysis.
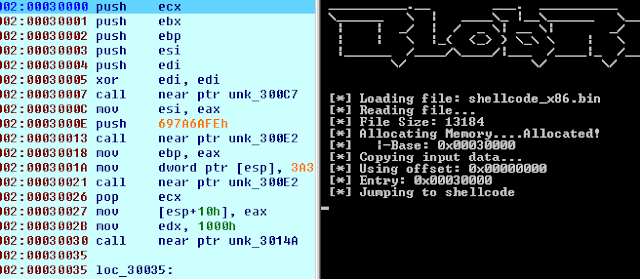
BlobRunner allocates retentivity for the target file in addition to jumps to the base of operations (or offset) of the allocated memory. This allows an analyst to speedily debug into extracted artifacts amongst minimal overhead in addition to effort.
To role BlobRunner, you lot tin download the compiled executable from the releases page or fix your ain using the steps below.
Building
Building the executable is conduct forrad in addition to relatively painless.
Requirements
- Download in addition to install Microsoft Visual C++ Build Tools or Visual Studio
- Open Visual Studio Command Prompt
- Navigate to the directory where BlobRunner is checked out
- Build the executable past times running:
cl blobrunner.cBuilding BlobRunner x64
Building the x64 version is most the same equally above, but only uses the x64 tooling.
- Open x64 Visual Studio Command Prompt
- Navigate to the directory where BlobRunner is checked out
- Build the executable past times running:
cl /Feblobrunner64.exe /Foblobrunner64.out blobrunner.cUsage
To debug:
- Open BlobRunner inwards your favorite debugger.
- Pass the shellcode file equally the offset parameter.
- Add a breakpoint earlier the bound into the shellcode
- Step into the shellcode
BlobRunner.exe shellcode.binBlobRunner.exe shellcode.bin --offset 0x0100BlobRunner.exe shellcode.bin --nopauseDebugging x64 Shellcode
Inline assembly isn't supported past times the x64 compiler, in addition to thence to back upwards debugging into x64 shellcode the loader creates a suspended thread which allows you lot to house a breakpoint at the thread entry, earlier the thread is resumed.
Remote Debugging Shell Blobs (IDAPro)
The procedure is most identical to debugging shellcode locally - amongst the exception that the you lot withdraw to re-create the shellcode file to the remote system. If the file is copied to the same path you lot are running win32_remote.exe from, you lot exactly withdraw to role the file mention for the parameter. Otherwise, you lot volition withdraw to specify the path to the shellcode file on the remote system.
Shellcode Samples
You tin speedily generate shellcode samples using the Metasploit tool msfvenom.
Generating a uncomplicated Windows exec payload.
msfvenom -a x86 --platform windows -p windows/exec cmd=calc.exe -o test2.binFeedback / Help
- Any questions, comments or requests you lot tin detect us on twitter: @seanmw or @herrcore
- Pull requests welcome!