Tidos-Framework V1.7 - The Offensive Manual Spider Web Application Penetration Testing Framework
TIDoS Framework is a comprehensive web-app audit framework.
let's proceed this simpleHighlights :-
The top dog highlights of this framework is:
- TIDoS Framework straight off boasts of a century+ of modules.
- A consummate versatile framework to comprehend upward everything from Reconnaissance to Vulnerability Analysis.
- Has five top dog phases, subdivided into 14 sub-phases consisting a total of 104 modules.
- Reconnaissance Phase has 48 modules of its ain (including active together with passive recon, information disclosure modules).
- Scanning & Enumeration Phase has got xv modules (including port scans, WAF analysis, etc)
- Vulnerability Analysis Phase has 36 modules (including most mutual vulnerabilites inward action).
- Exploits Castle has alone 1 exploit.
(purely developmental) - And finally, Auxillaries bring got 4 modules.
under dev. - All iv phases each bring a
Auto-Awesomemodule which automates every module for you. - You simply demand the domain, together with locomote out everything is to this tool.
- TIDoS has total verbose out support, together with then you'll know whats going on.
- Fully user friendly interaction environment.
(no shits)
Installation :
- Clone the repository locally together with navigate there:
git clone https://github.com/theinfecteddrake/tidos-framework.git cd tidos-framework- Install the dependencies:
chmod +x install ./installThats it! Now yous are skilful to go! Now lets run the tool:
tidosGetting Started :-
TIDoS is made to last comprehensive together with versatile. It is a highly flexible framework where yous simply bring to conduct together with usage modules.
But earlier that, yous demand to ready your ain
API KEYS for diverse OSINT purposes. To create so, opened upward up API_KEYS.py nether files/ directory together with ready your ain keys together with access tokens for SHODAN, CENSYS, FULL CONTACT, GOOGLE together with WHATCMS. Public API KEYS together with ACCESS TOKENS for SHODAN together with WHATCMS bring been provided amongst the TIDoS unloosen itself. You tin give the sack nonetheless add together your own... no harm!Finally, equally the framework opens up, locomote into the website refer
eg. http://www.example.com together with allow TIDoS Pb you. Thats it! Its equally slow equally that.Recommended:To update this tool, usage
- Follow the enterprise of the tool (Run inward a schematic way).
Reconnaissance ➣ Scanning & Enumeration ➣ Vulnerability Analysis
tidos_updater.py module nether tools/ folder.Flawless Features :-
TIDoS Framework shortly supports the following:
and is nether active development- Reconnaissance + OSINT
- Passive Reconnaissance:
- Nping Enumeration
Via external APi - WhoIS Lookup
Domain information gathering - GeoIP Lookup
Pinpoint physical location - DNS Configuration Lookup
DNSDump - Subdomains Lookup
Indexed ones - Reverse DNS Lookup
Host Instances - Reverse IP Lookup
Hosts on same server - Subnets Enumeration
Class Based - Domain IP History
IP Instances - Web Links Gatherer
Indexed ones - Google Search
Manual search - Google Dorking (multiple modules)
Automated - Email to Domain Resolver
Email WhoIs - Wayback Machine Lookups
Find Backups - Breached Email Check
Pwned Email Accounts - Enumeration via Google Groups
Emails Only - Check Alias Availability
Social Networks - Find PasteBin Posts
Domain Based - LinkedIn Gathering
Employees & Company - Google Plus Gathering
Domain Profiles - Public Contact Info Scraping
FULL CONTACT - Censys Intel Gathering
Domain Based - Threat Intelligence Gathering
Bad IPs
- Nping Enumeration
- Active Reconnaissance
- Ping Enumeration
Advanced - CMS Detection
(185+ CMSs supported)IMPROVED - Advanced Traceroute
IMPROVED robots.txttogether withsitemap.xmlChecker- Grab HTTP Headers
Live Capture - Find HTTP Methods Allowed
via OPTIONS - Detect Server Type
IMPROVED - Examine SSL Certificate
Absolute - Apache Status Disclosure Checks
File Based - WebDAV HTTP Enumeration
PROFIND & SEARCH - PHPInfo File Enumeration
via Bruteforce - Comments Scraper
Regex Based - Find Shared DNS Hosts
Name Server Based - Alternate Sites Discovery
User-Agent Based - Discover Interesting Files
via Bruteforce- Common Backdoor Locations
shells, etc. - Common Backup Locations
.bak, .db, etc. - Common Password Locations
.pgp, .skr, etc. - Common Proxy Path Configs.
.pac, etc. - Common Dot Files
.htaccess, .apache, etc
- Common Backdoor Locations
- Ping Enumeration
- Information Disclosure
- Credit Cards Disclosure
If Plaintext - Email Harvester
IMPROVED - Fatal Errors Enumeration
Includes Full Path Disclosure - Internal IP Disclosure
Signature Based - Phone Number Havester
Signature Based - Social Security Number Harvester
US Ones
- Credit Cards Disclosure
- Passive Reconnaissance:
- Scanning & Enumeration
- Remote Server WAF Enumeration
Generic54 WAFs - Port Scanning
Ingenious Modules- Simple Port Scanner
via Socket Connections - TCP SYN Scan
Highly reliable - TCP Connect Scan
Highly Reliable - XMAS Flag Scan
Reliable Only inward LANs - Fin Flag Scan
Reliable Only inward LANs - Port Service Detector
- Simple Port Scanner
- Web Technology Enumeration
Absolute - Operating System Fingerprinting
IMPROVED - Banner Grabbing of Services
via Open Ports - Interactive Scanning amongst NMap
16 preloaded modules - Enumeration Domain-Linked IPs
Using CENSYS Database - Web together with Links Crawlers
- Depth 1
Indexed Uri Crawler - Depth 2
Single Page Crawler - Depth three
Web Link Crawler
- Depth 1
- Remote Server WAF Enumeration
- Vulnerability Analysis
Web-Bugs & Server Misconfigurations
- Insecure CORS
Absolute - Same-Site Scripting
Sub-domain based - Zone Transfer
DNS Server based - Clickjacking
- Frame-Busting Checks
X-FRAME-OPTIONSHeader Checks
- Security on Cookies
HTTPOnlyFlagSecureFlag
- Cloudflare Misconfiguration Check
- DNS Misconfiguration Checks
- Online Database Lookup
For Breaches
- HTTP Strict Transport Security Usage
- HTTPS Enabled but no HSTS
- Domain Based Email Spoofing
- Missing
SPFRecords - Missing
DMARCRecords
- Missing
- Host Header Injection
- Port Based
Over HTTP 80 X-Forwarded-ForHeader Injection
- Port Based
- Security Headers Analysis
Live Capture - Cross-Site Tracing
HTTP TRACE Method - Session Fixation
via Cookie Injection - Network Security Misconfig.
- Checks for
TELNETEnabledvia Port 23
- Checks for
- File Inclusions
- Local File Inclusion (LFI)
Param based - Remote File Inclusion (RFI)
IMPROVED- Parameter Based
- Pre-loaded Path Based
- Local File Inclusion (LFI)
- OS Command Injection
Linux & Windows (RCE) - Path Traversal
(Sensitive Paths) - Cross-Site Request Forgery
Absolute - SQL Injection
- Error Based Injection
- Cookie Value Based
- Referer Value Based
- User-Agent Value Based
- Auto-gathering
IMPROVED
- Blind Based Injection
Crafted Payloads- Cookie Value Based
- Referer Value Based
- User-Agent Value Based
- Auto-gathering
IMPROVED
- Error Based Injection
- LDAP Injection
Parameter Based - HTML Injection
Parameter Based - Bash Command Injection
ShellShock - XPATH Injection
Parameter Based - Cross-Site Scripting
IMPROVED- Cookie Value Based
- Referer Value Based
- User-Agent Value Based
- Parameter Value Based
Manual
- Unvalidated URL Forwards
Open Redirect - PHP Code Injection
Windows + Linux - HTTP Response Splitting
CRLF Injection- User-Agent Value Based
- Parameter value Based
Manual
- Sub-domain Takeover
50+ Services- Single Sub-domain
Manual - All Subdomains
Automated
- Single Sub-domain
- PlainText Protocol Default Credential Bruteforce
- FTP Protocol Bruteforce
- SSH Protocol Bruteforce
- POP 2/3 Protocol Bruteforce
- SQL Protocol Bruteforce
- XMPP Protocol Bruteforce
- SMTP Protocol Bruteforce
- TELNET Protocol Bruteforce
- Insecure CORS
- Auxillary Modules
- Hash Generator
MD5, SHA1, SHA256, SHA512 - String & Payload Encoder
7 Categories - Forensic Image Analysis
Metadata Extraction - Web HoneyPot Probability
ShodanLabs HoneyScore
- Hash Generator
- Exploitation
purely developmental
- ShellShock
Other Tools:
net_info.py- Displays information close your network. Located nethertools/.tidos_updater.py- Updates the framework to the latest unloosen via signature matching. Located nether `tools/'.
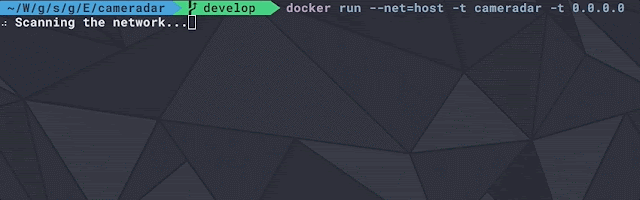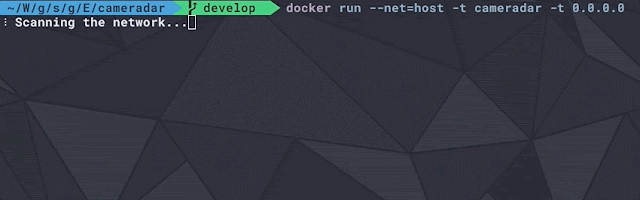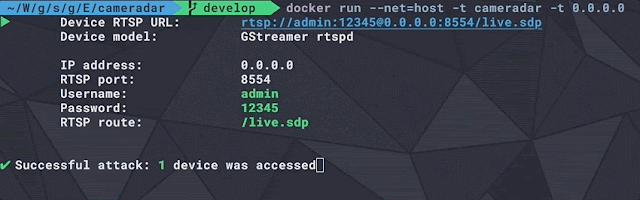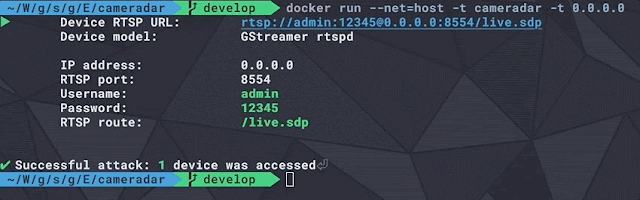
TIDoS In Action:
Version:
v1.7 [latest release] [#stable]Upcoming:
These are about modules which I bring idea of adding:
- Some to a greater extent than of Enumeraton & Information Disclosure modules.
- Lots to a greater extent than of OSINT & Stuff (let that last a suspense).
- More of Auxillary Modules.
- Some Exploits are besides existence worked on.
Ongoing:
- Working on a full-featured Web UI implementation on Flask together with MongoDB together with Node.js.
- Working on a novel framework, a existent framework.
To last released amongst v2 - Working on a motility characteristic + add-on of arguments.
- Normal Bug Fixing Stuffs.
As per the issues existence raised - Some other perks:
- Working on a agency for contributing novel modules easily.
- A consummate novel method of multi-threaded fuzzing of parameters.
- Keeping improve of novel console stuff.