Sniffglue - Secure Multithreaded Bundle Sniffer
sniffglue is a network sniffer written inward rust. Network packets are parsed concurrently using a thread puddle to utilize all cpu cores. Project goals are that you lot tin sack run sniffglue securely on untrusted networks as well as that it must non crash when processing packets. The output should live equally useful equally possible yesteryear default.
Usage
sniffglue enp0s25Installation
There is an official packet available for archlinux:
pacman -S sniffgluelibpcap-dev libseccomp-dev, Archlinux: libpcap libseccomp.cargo install sniffglueProtocols
- ethernet
- ipv4
- ipv6
- arp
- tcp
- udp
- icmp
- http
- tls
- dns
- dhcp
- cjdns eth beacons
- ssdp
- dropbox beacons
- 802.11
Docker
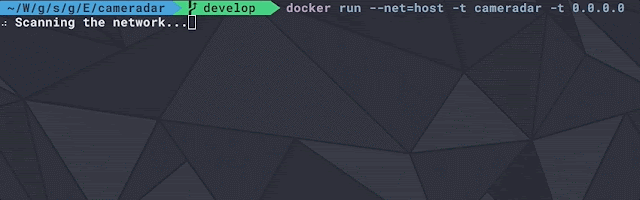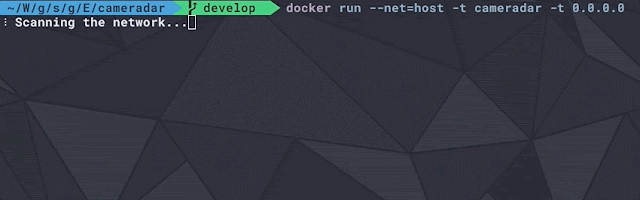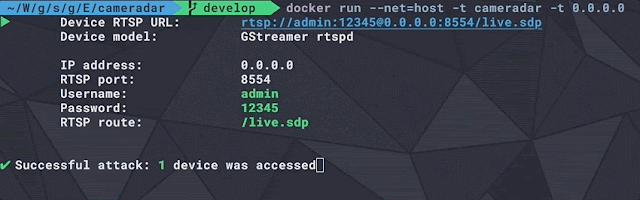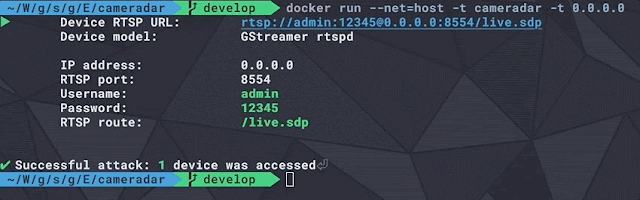
You tin sack construct sniffglue equally a docker icon to debug container setups. The icon is currently close 11.1MB. It is recommended to force it to your ain registry.
docker construct -t sniffglue . docker run -it --init --rm --net=host sniffglue eth0Security
To written report a safety resultant delight contact kpcyrd on ircs://irc.hackint.org.
Seccomp
To ensure a compromised procedure doesn't compromise the system, sniffglue uses seccomp to trammel the syscalls that tin sack live used afterward the procedure started. This is done inward 2 stages, foremost at the rattling commencement (directly afterward env_logger initialized) as well as in i lawsuit afterward the sniffer has been setup, but earlier packets are read from the network.
Hardening
During the instant stage, there's besides unopen to full general hardening that is applied earlier all unneeded syscalls are lastly disabled. Those are organisation specific, then a configuration file is read from
/etc/sniffglue.conf. This config file specifies an empty directory for chroot as well as an unprivileged trouble concern human relationship inward user that is used to drib root privileges.boxxy-rs
This projection includes a minor boxxy-rs based trounce that tin sack live used to explore the sandbox at diverse stages during as well as afterward initialization. This is besides used yesteryear travis to ensure the sandbox genuinely blocks syscalls.
cargo run --example boxxyReproducible builds
This projection is tested using reprotest. Currently the next variations are excluded:
-time- needed because the crates.io cert expires inward the future-domain_host- requires root for unshare(2) as well as has been excluded
ci/reprotest.shFuzzing
The packet processing of sniffglue tin sack live fuzzed using cargo-fuzz. Everything you lot should demand is provided inward the
fuzz/ directory that is distributed along alongside its source code. Please banking concern complaint that this programme links to libpcap which is non included inward the electrical flow fuzzing configuration.cargo fuzz run read_packet