Malice - Virustotal Wanna Move (Now Alongside 100% To A Greater Extent Than Hipster)
Malice's mission is to live a costless opened upwards source version of VirusTotal that anyone tin give notice role at whatever scale from an independent researcher to a fortune 500 company.
Try It Out
DEMO: demo.malice.io
- username:
malice - password:
ecilam
Requirements
Hardware
- 16GB disk space
- 4GB RAM
Software
Getting Started (OSX)
Install
$ brew install maliceio/tap/maliceUsage: malice [OPTIONS] COMMAND [arg...] Open Source Malware Analysis Framework Version: 0.3.11 Author: blacktop - <https://github.com/blacktop> Options: --debug, -D Enable debug trend [$MALICE_DEBUG] --help, -h demo assistance --version, -v impress the version Commands: scan Scan a file lookout Watch a folder lookup Look upwards a file hash elk Start an ELK docker container plugin List, Install or Remove Plugins assistance Shows a listing of commands or assistance for i ascendancy Run 'malice COMMAND --help' for to a greater extent than information on a command.Scan about malware
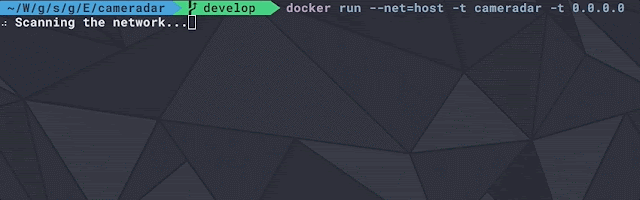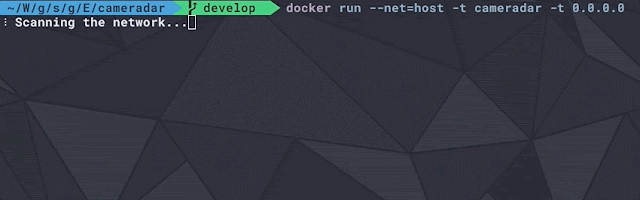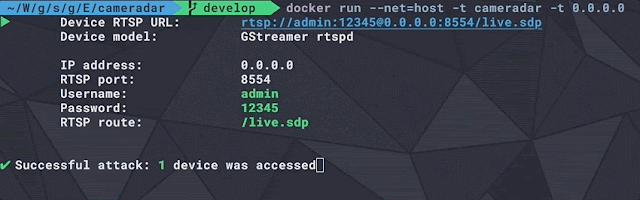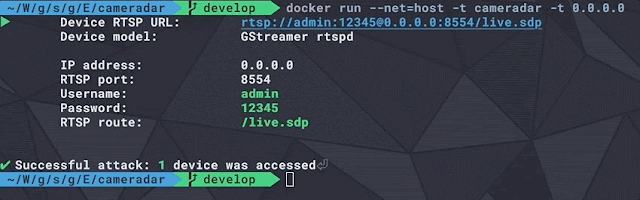
$ malice scan evil.malwareNOTE: On the showtime run malice volition download all of it's default plugins which tin give notice accept a piece to complete.Malice volition output the results every bit a markdown tabular array that tin give notice live piped or copied into a results.md that volition await cracking on Github run across here
Start Malice's Web UI
$ malice elkYou tin give notice opened upwards the Kibana UI as well as await at the scan results here: http://localhost (assuming you lot are using Docker for Mac)
- Type inwards malice every bit the
Index mention or patternas well as click Create.
- Now click on the
Malice Tabas well as behold!!!
Getting Started (Docker inwards Docker)
Install/Update all Plugins
docker run --rm -v /var/run/docker.sock:/var/run/docker.sock malice/engine plugin update --allScan a file
docker run --rm -v /var/run/docker.sock:/var/run/docker.sock \ -v `pwd`:/malice/samples \ -e MALICE_VT_API=$MALICE_VT_API \ malice/engine scan SAMPLEDocumentation